Bill Gates phishing campaign 'nearly identical' to Twitter attack

A phishing campaign has been targeting recipients by posing as a legitimate communication from the Bill and Melinda Gates Foundation and others, according to cybersecurity and phishing protection firm Area 1 Security.
The campaign came a day after Twitter was roiled by an external group gaining access to the social media platform’s controls from the inside. During that takeover, Bill Gates’ account posted a message that was “nearly identical” to the phishing attempt, Area 1 pointed out.
During the hack many high profile accounts including Joe Biden and Elon Musk were targeted. Area 1 said the phishing scam also involves other impersonations beyond gates — like Fortune 500 companies.
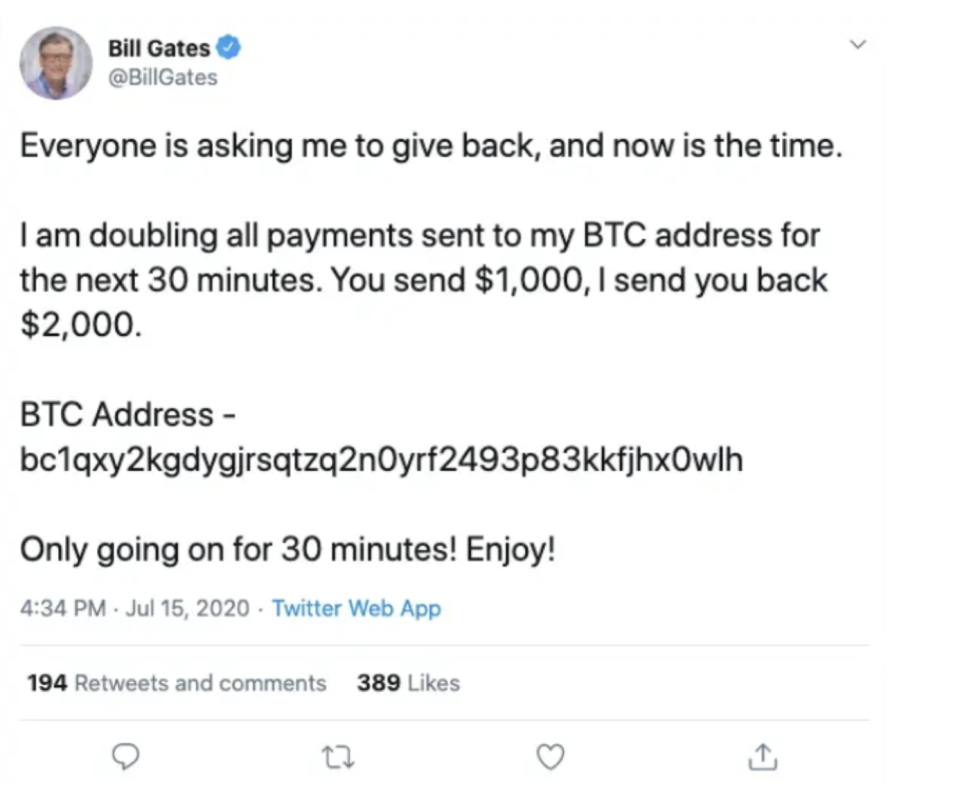
"Hello all, everyone is asking me to give back and now is the time," the phishing email read. "I am doubling all payments sent to my BTC address for the next 7 days. You send $1,000, I send you back $2,000."

“Only going for 7 days! Enjoy,” the email said.
Just a day earlier, Gates’s public Twitter posted a very similar message, down to “Only going on for 30 minutes! Enjoy!”
According to Area 1, the phishing attack used a domain with one letter change that often is overlooked: "gatesfoundatlon" rather than "gatesfoundation" as well as a .com suffix. The attacker also added a type of record called SPF that helps to ensure delivery of an email through spam folders as it makes it look more legitimate.
The domain name “gatesfoundatlon.com” was registered just after midnight on the morning of June 16, but the domain lookup showed that the identity of the account was protected by a domain privacy company.
In the Twitter scam, around $118,000 worth of bitcoin was sent in around three hours — a paltry sum for the level of sophistication for the attack, which led many experts to conclude that the attack was likely a test or the beginning of something.
It’s not yet clear whether the phishing campaign and its near-identical language and timing means that there is a relationship between the two attacks or whether a copycat situation is at play.
-
Ethan Wolff-Mann is a writer at Yahoo Finance focusing on consumer issues, personal finance, retail, airlines, and more. Follow him on Twitter @ewolffmann.
A list of major businesses that require masks: Walmart, CVS, Starbucks, Target, and more
The 2008 recession was far worse for young people's careers than previously thought
Black-owned small businesses continue to face harsh cash crunch
Workers on re-openings: 'I would like to never go back to the office'